Module 3: IAM Policies Assignment
Problem Statement: You work for XYZ Corporation. To maintain the security of the AWS account and the resources you have been asked to implement a solution that can help easily recognize and monitor the different users.
Tasks To Be Performed:
- Create policy number 1 which lets the users to: a. Access S3 completely b. Only create EC2 instances c. Full access to RDS
- Create a policy number 2 which allows the users to: a. Access CloudWatch and billing completely b. Can only list EC2 and S3 resources
- Attach policy number 1 to the
DevTeamfrom task 1- Attach policy number 2 to
OpsTeamfrom task 1
Task 1: Creating Policy Number 1
First, I logged into the AWS Management Console and navigated to the IAM dashboard. From there, I clicked on the Policies tab on the left sidebar to begin creating a new policy.
I clicked the Create policy button and then switched to the JSON tab. Here, I pasted in the JSON policy that allows for full S3 access, EC2 instance creation only, and full RDS access.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "rds:*",
"Resource": "*"
}
]
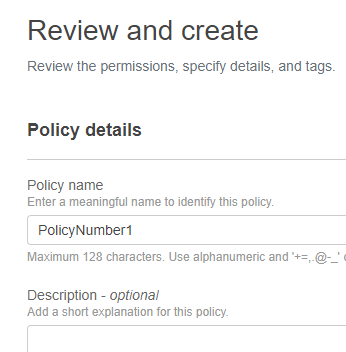
}After reviewing the policy to make sure it met the requirements, I named the policy PolicyNumber1 and clicked Create policy.
Task 2: Creating Policy Number 2
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"cloudwatch:*",
"aws-portal:*"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ec2:DescribeInstances",
"s3:List*"
],
"Resource": "*"
}
]
}Continuing in the IAM dashboard, I clicked on the Policies tab again and then clicked the Create policy button. I switched over to the JSON tab, just like before, and pasted in the JSON policy for allowing full access to CloudWatch and billing as well as the ability to only list EC2 and S3 resources. After reviewing this second policy, I named it PolicyNumber2 and clicked Create policy.
Task 3: Attaching Policy Number 1 to the DevTeam
Next, I moved on to attaching PolicyNumber1 to the DevTeam. I clicked on the User groups tab on the left sidebar and selected the D evTeam group by clicking its name.
Within the DevTeam group interface, I clicked the Permissions tab, Add permissions button and Attach policies.
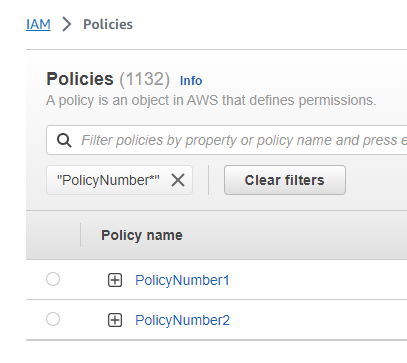
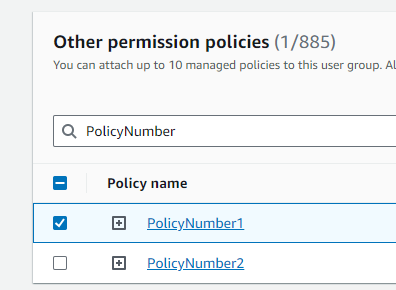
A list of available policies appeared, and I searched for PolicyNumber1. Upon finding it, I selected it and then clicked the Attach policies button.
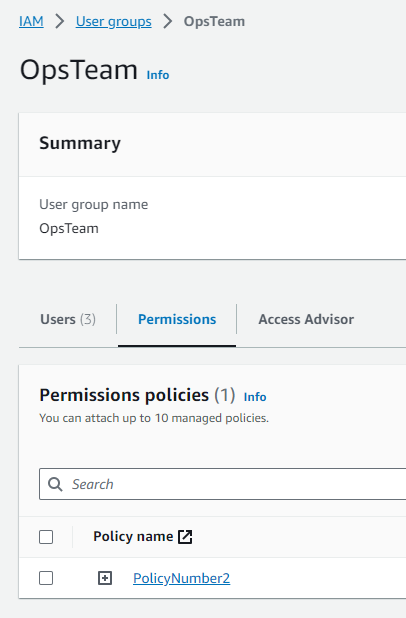
Task 4: Attaching Policy Number 2 to the OpsTeam
Finally, to attach PolicyNumber2 to the OpsTeam, I went back to the User groups tab and clicked on the OpsTeam group.
Just like with the DevTeam, while inside the OpsTeam group interface I clicked the Permissions tab, Add permissions button and Attach policies. I searched for PolicyNumber2 selected it from the list, and then clicked the Attach policies button.