Module 3: Case Study - 1
Problem Statement: You work for XYZ Corporation that uses on premise solutions and a limited number of systems. With the increase in requests in their application, the load also increases. So, to handle the load the corporation has to buy more systems almost on a regular basis. Realizing the need to cut down the expenses on systems, they decided to move their infrastructure to AWS. Tasks To Be Performed: 1. a. Create a user account that can login to the console b. Create a group and make sure that the group can only launch and stop EC2 instances using that previously created account 2. a. Provide permission to let the user of a previously created account to create VPCs, Subnets, NACL and security groups b. Further add the permission so that the user can create RDS instance c. Explore security options to protect the AWS resources and secure the permissions provided to the group
Part 1-A
Create a user account named User4 that can login to the console:
- I opened the AWS Management Console.
- I navigated to the
IAM(Identity and Access Management) dashboard. - On the navigation pane, I clicked on
Usersand then selectedCreate user. - I entered the username as
User4. - I selected
Provide user access to the AWS Management Consoleand set a console password. - In Set Permissions
Add user to groupwas selected so I clicked onCreate Group
Part 1-B
Create a group for User4 to launch and stop EC2 instances:
- I provided a suitable group name
User4Group. - I attached permissions by choosing
Create policy. In the JSON editor, I input the policy to allow launching and stopping EC2 instances.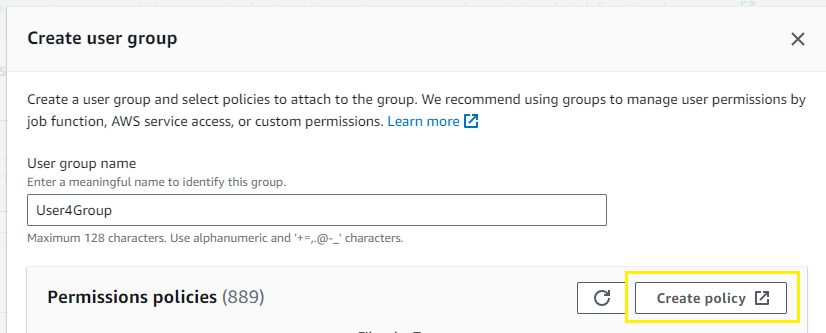
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:RunInstances", // Allows launching instances
"ec2:StopInstances" // Allows stopping instances
],
"Resource": "*"
}
]
}- I reviewed and created the policy
RunStopEC2 - I attached this policy to the group as I created it.
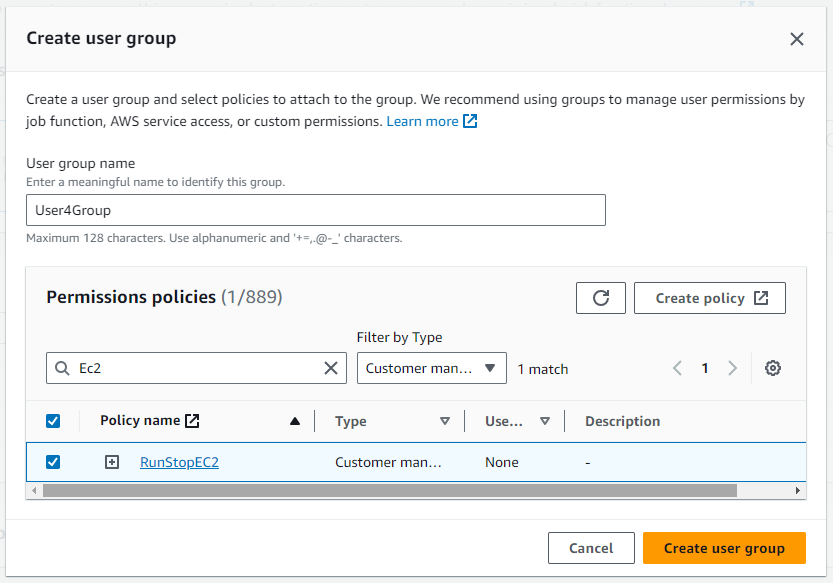
Summary
I created a new user named
User4. During this process, I was prompted to attachUser4to a group. Instead of choosing an existing group, I createdUser4Group. While setting upUser4Group, I was given the option to attach a policy. Instead of selecting a pre-existing one, I created a new policy namedRunStopEC2. Finally, theUser4Groupwas created withUser4in it and theRunStopEC2policy attached to it.
Part 2-A
I provided permissions for User4 to create VPCs, Subnets, NACL, and security groups:
- On the IAM dashboard, I clicked on
Policiesfrom the left sidebar. - I then clicked the
Create policybutton. - On the “Create Policy” page, I switched to the “JSON” tab.
- I pasted the following permissions to allow
User4to create VPCs, Subnets, NACLs, and security groups:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:CreateVpc",
"ec2:CreateSubnet",
"ec2:CreateNetworkAcl",
"ec2:CreateSecurityGroup"
],
"Resource": "*"
}
]
}-
Named the policy
VPC_Sub_NACL_SG -
After reviewing, I created the policy.
-
I navigated to
User groupsand selectedUser4Groupthe group associated withUser4. -
In
Permissionstab I clickedAdd permissions. -
I attached
VPC_Sub_NACL_SGpolicy to the group.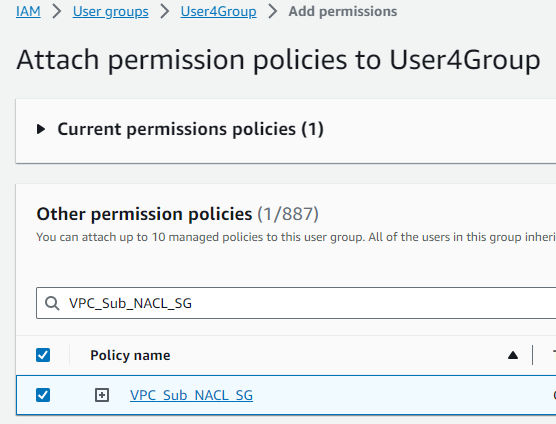
Part 2-B
I added the permission so that User4 can create an RDS instance:
- I repeated the steps above to create and attach a policy named
Create_RDSwhich has the following
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "rds:CreateDBInstance",
"Resource": "*"
}
]
}Part 2-C
I explored security options to protect the AWS resources and secure the permissions for the group:
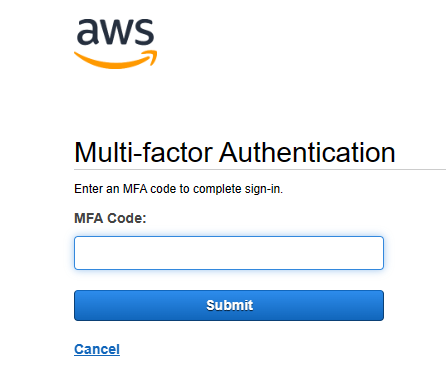
- MFA: I enabled MFA for
User4, adding an additional layer of security for console logins.
- Fine-grained Policies: I ensured that the policies I created granted only necessary permissions to avoid excessive privileges.