Project - 3: Publishing Amazon SNS Messages Privately
Industry: Healthcare
Problem Statement: How to secure patient records online and send it privately to the intended party
Topics: In this project, you will be working on a hospital project to send reports online and develop a platform so the patients can access the reports via mobile and push notifications. You will publish the report to an Amazon SNS keeping it secure and private. Your message will be hosted on an EC2 instance within your Amazon VPC. By publishing the messages privately, you can improve the message delivery and receipt through Amazon SNS.
Highlights:
- AWS CloudFormation to create a VPC
- Connect VPC with AWS SNS
- Publish message privately with SNS
To clone the repository that contains the CloudFormation templates, I use the following command and link:
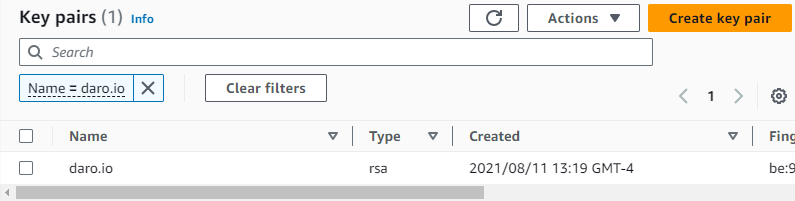
git clone https://github.com/aws-samples/aws-sns-samples.gitStep 1: EC2 Key Pair
I have will make usre of a private key I already have
Step 2: Create the AWS Resource
Template
SNS-VPCE-Tutorial-CloudFormation.template
The provided CloudFormation template defines a set of AWS resources for setting up a VPC and related components for an SNS VPC Endpoints tutorial. Here’s a summary of the resources it creates and their purposes:
I navigate to CloudFormation Dashboard and click “Create stack”
-
Step 1: Create stack
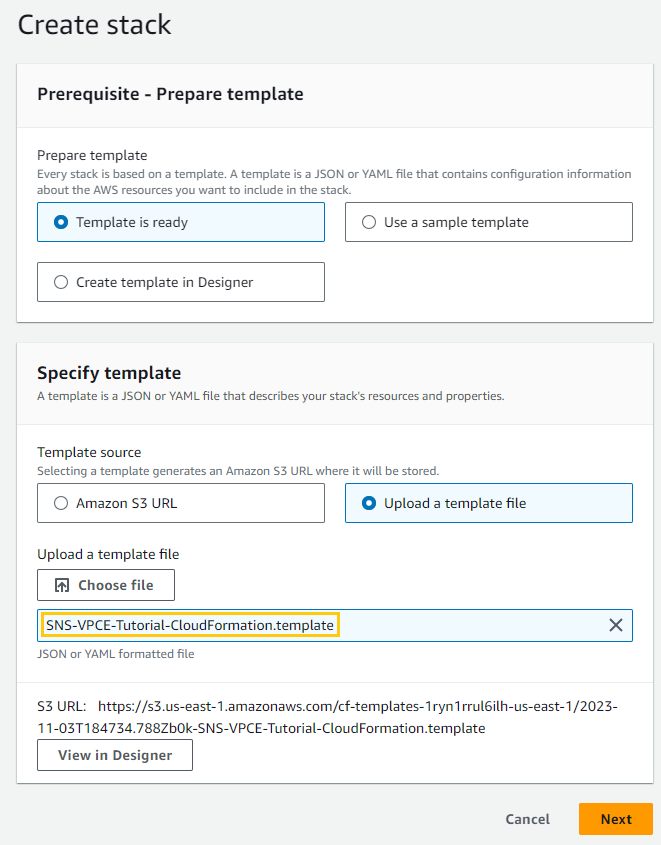 We upload the template
We upload the template -
Step 2: Specify stack details
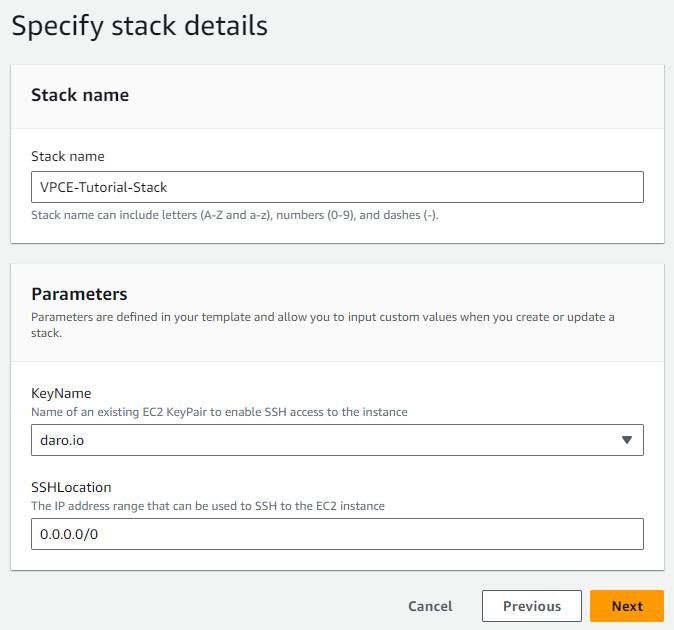 After naming the stack, I fill in the ‘KeyName’ parameter with the name of an existing EC2 KeyPair to enable SSH access. I set the ‘SSHLocation’ parameter to ‘0.0.0.0/0’, which allows SSH connections from any IP address.
After naming the stack, I fill in the ‘KeyName’ parameter with the name of an existing EC2 KeyPair to enable SSH access. I set the ‘SSHLocation’ parameter to ‘0.0.0.0/0’, which allows SSH connections from any IP address. -
Step 3: Configure stack options Left all options at their default settings.
-
Step 4: Review
Step 3: Confirming the EC2 Instance lacks internet access
First, I’ll need to establish an SSH connection, it is necessary to obtain the EC2 instance’s public IP address.
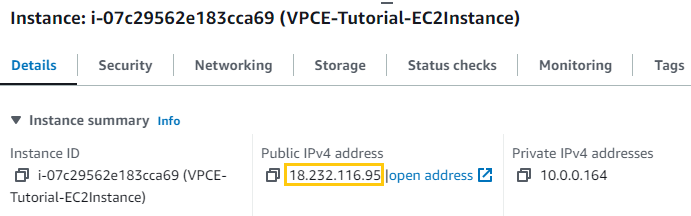
Using the Public IP I ssh into the EC2
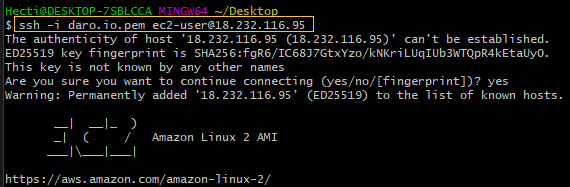
Using ping verifies instance’s lack of internet connectivity:
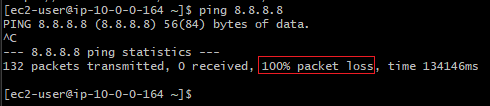
To verify that the instance lacks connectivity to Amazon SNS:
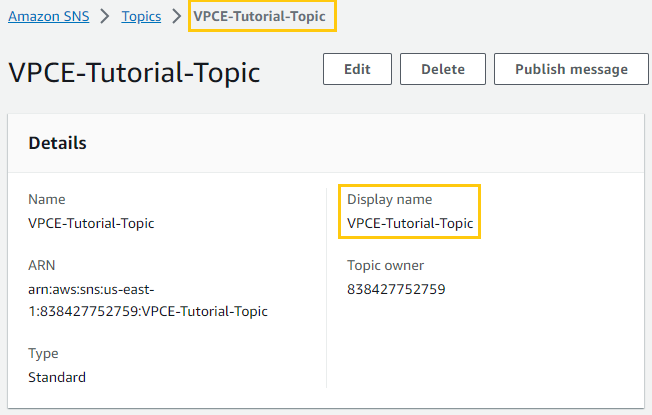
Using AWS CLI I attempt to publish a message SNS topic VPCE-Tutorial-Topic
aws sns publish --region us-east-1 --topic-arn arn:aws:sns:us-east-1:838427752759:VPCE-Tutorial-Topic --message "Hello"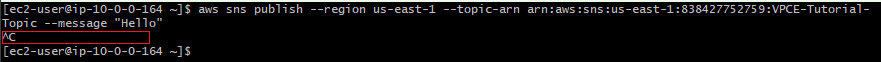 No message is published
No message is published
Step 4: VPC Endpoint for Amazon SNS
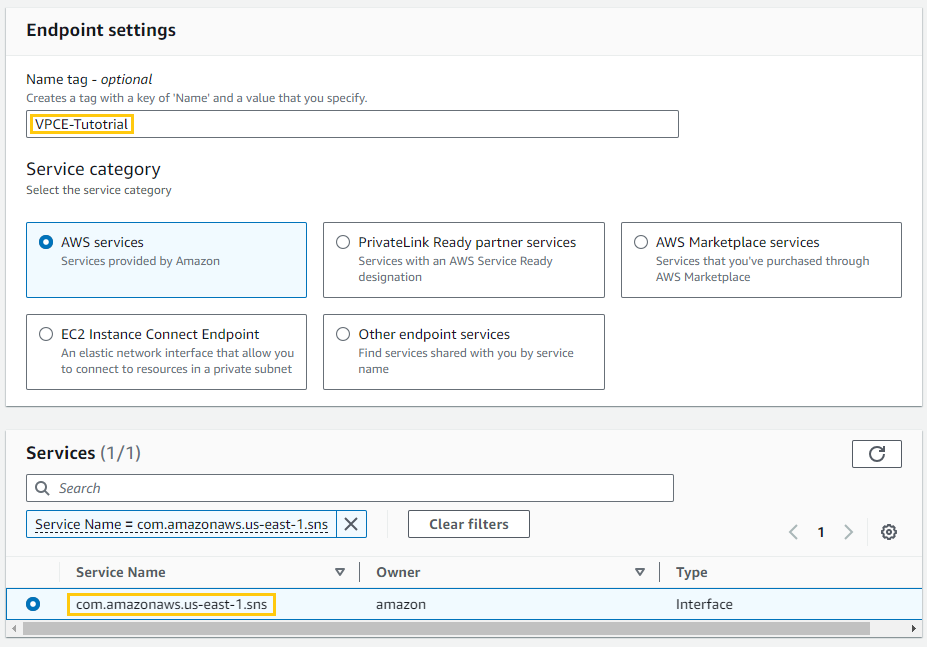
I begin by assigning the endpoint a Name Tag: ‘VPCE-Tutorial’. Under Services, I select the AWS service that the endpoint will connect to, which is the Simple Notification Service (SNS) in the US East (N. Virginia) region, identified by com.amazonaws.us-east-1.sns.
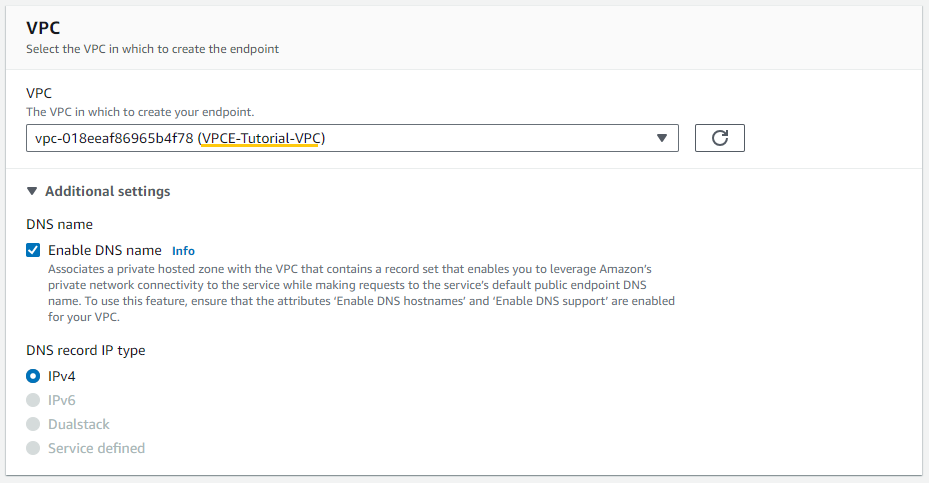
 I ensure that I select the VPC that was created from the CloudFormation template.
I ensure that I select the VPC that was created from the CloudFormation template.
 I select the ‘Tutorial Security Group’ as the Security Group, which was previously established by the CloudFormation template.
I select the ‘Tutorial Security Group’ as the Security Group, which was previously established by the CloudFormation template.
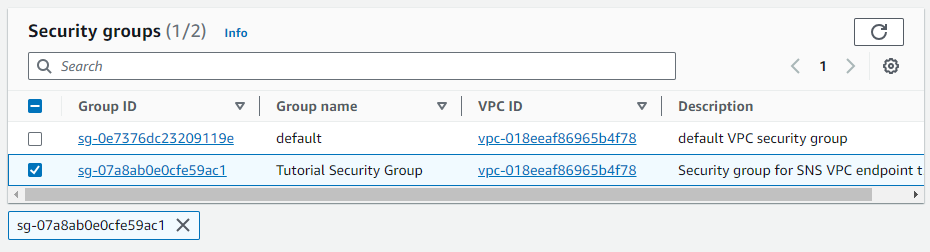
Step 5: Publish a message to SNS topic
Once again, I use the AWS CLI to publish a message to the SNS topic VPCE-Tutorial-Topic.
aws sns publish --region us-east-1 --topic-arn arn:aws:sns:us-east-1:838427752759:VPCE-Tutorial-Topic --message "Hello"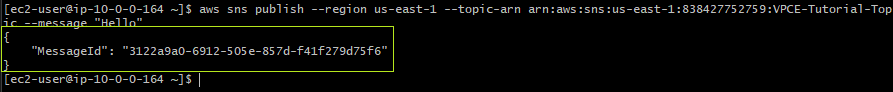
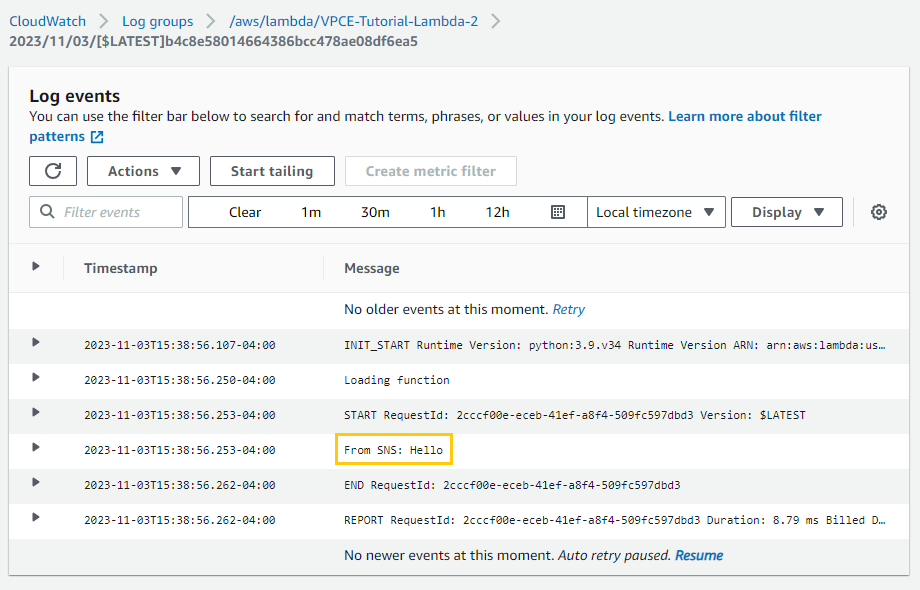
Step 6: Message deliveries verification
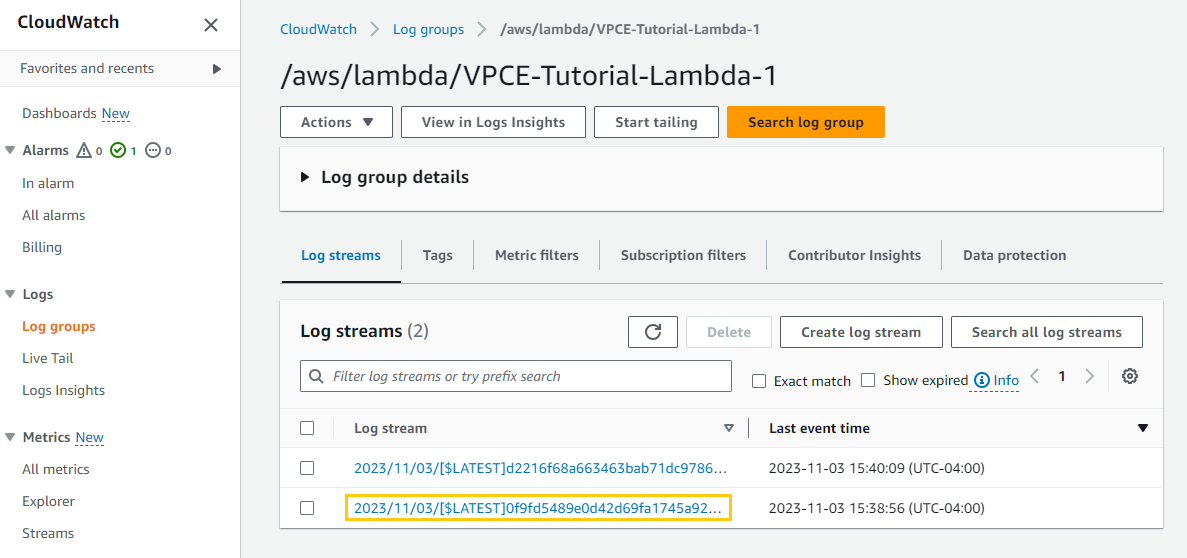
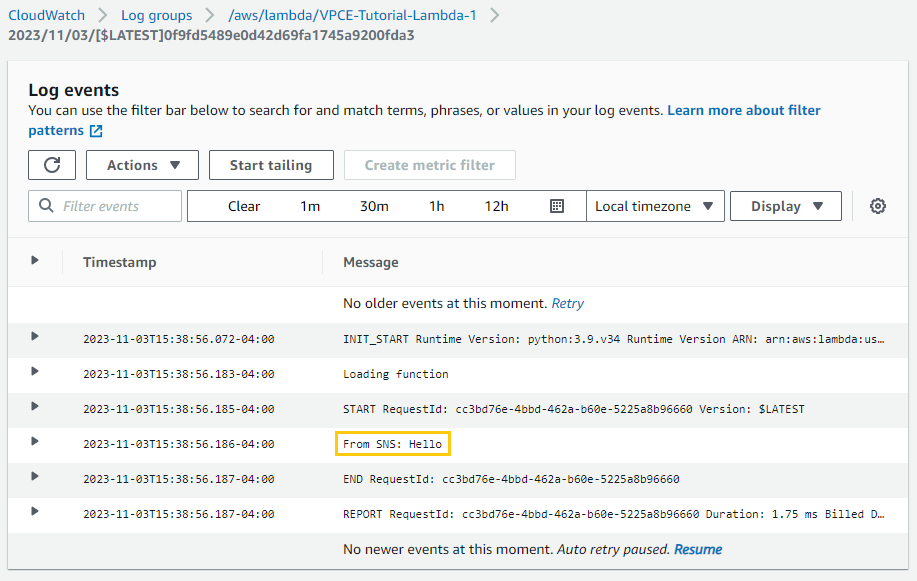
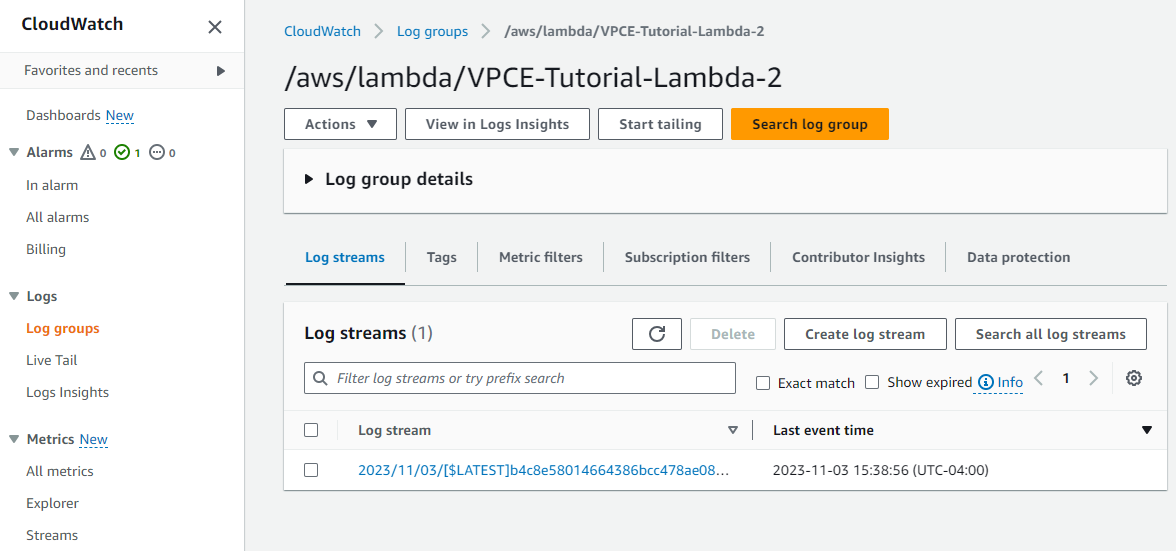
To verify that the Lambda functions were invoked
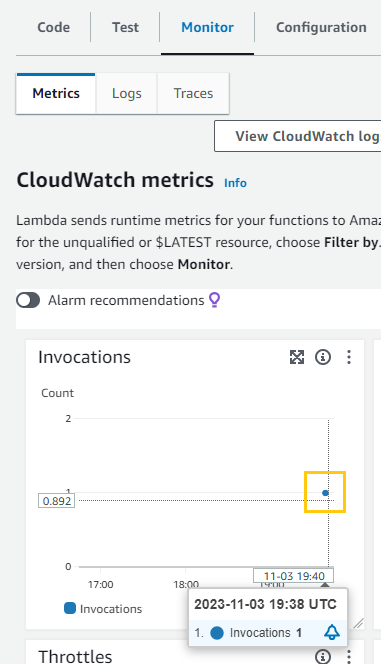
To verify that the CloudWatch logs were updated:
VPCE-Tutorial-Lambda-1
Success
VPCE-Tutorial-Lambda-2
Success
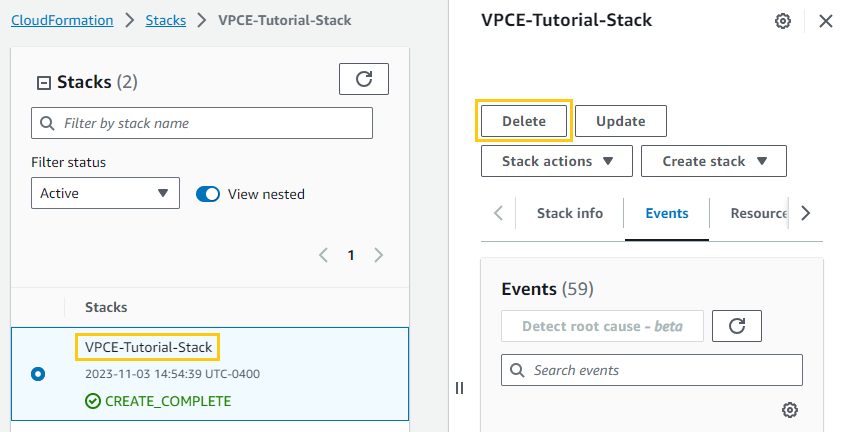
Step 7: Clean Up
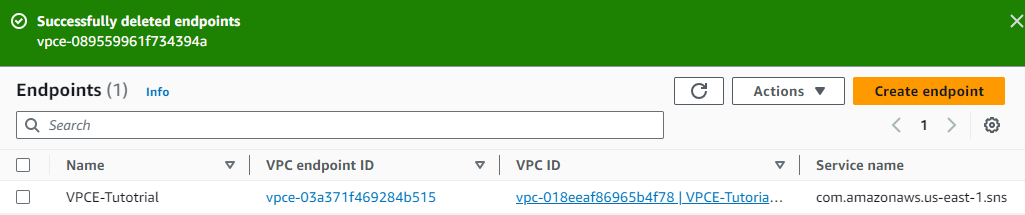
To delete the VPC endpoint:
I go to Actions > Delete VPC endpoints

To delete the AWS CloudFormation stack: