Module 7: Kubernetes Assignment - 5
Tasks To Be Performed:
- Use the previous deployment
- Deploy an NGINX deployment of 3 replicas
- Create an NGINX service of type ClusterIP
- Create an ingress service/ Apache to Apache service/ NGINX to NGINX service
%%Referencing Lecture 8 – Creating An Ingress
Not used
Ingress:
Ingress install from Hands-On-–-Kubernetes-Installation.pdf
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v0.49.0/deploy/static/provider/baremetal/deploy.yaml
%%
Step 1:
Continuing from Assignment 4
Instances and Their Private IP Addresses
k-master:
10.0.1.82worker1:10.0.1.57worker2:10.0.1.119
Step 2:
I use the deployment from Assignment 1 Step 2: NGINX Deployment
Step 3:
I’ll use the ClusterIP service we converted from NodePort in Assignment 4 Step 2: Changing Service
Step 4: Installing Ingress Controller
Next, I install the Nginx Ingress Controller which allows us to manage Ingress resources and control external traffic into the cluster. Ingress resources are used to configure rules for routing incoming external requests to specific services or pods within the cluster. To do this, I use the official deployment YAML file provided by the project. GitHub: Bare metal clusters
This command fetches the deployment YAML file from the official GitHub repository and applies it to the cluster.
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.8.2/deploy/static/provider/baremetal/deploy.yaml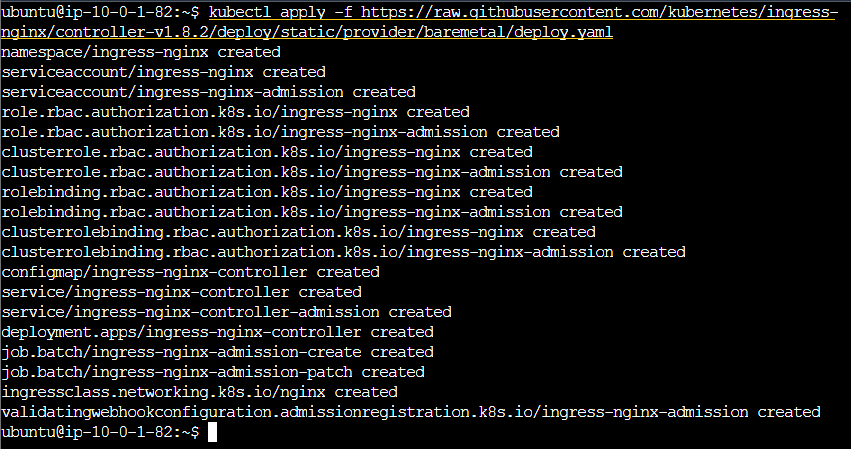
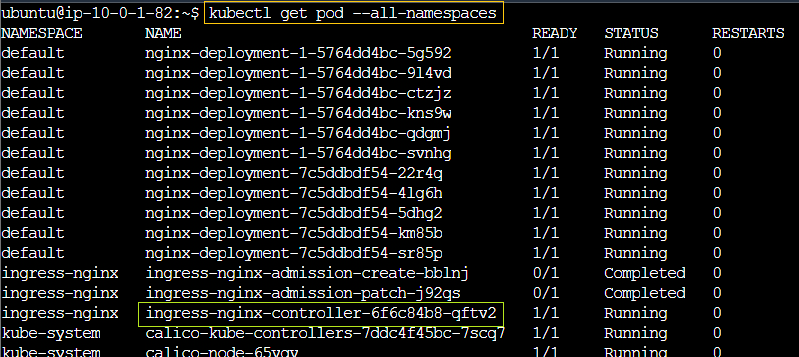
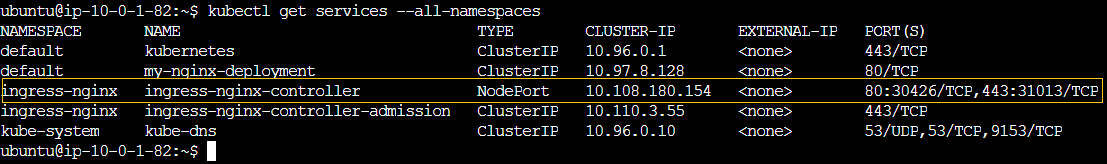
We can confirm that the Nginx Ingress Controller is successfully running within our Kubernetes cluster as a pod
We have an ingress service configured with NodePort types on the following ports:
- HTTP: 80, mapped to 30426
- HTTPS: 443, mapped to 31013”
 %%
The Public IP that worked was worker2
Need to find
%%
The Public IP that worked was worker2
Need to find
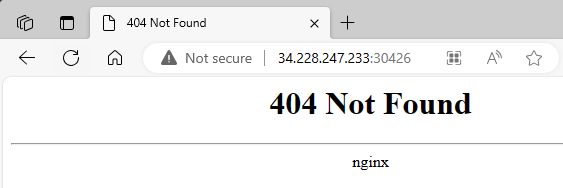
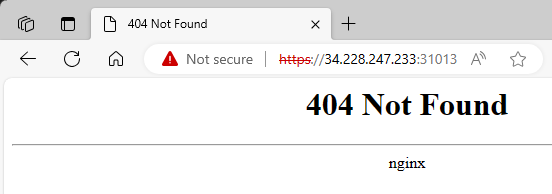 Seem like this works with the Public IP of the node that runs at least one pod
kubectl get pods -o wide
#question
Seem like this works with the Public IP of the node that runs at least one pod
kubectl get pods -o wide
#question
The above theory seem incorrect according to ChatGPT
With a NodePort service in Kubernetes, you can access the service using the public IP address of any node in the cluster along with the NodePort, regardless of which node the pod is actually running on.
Enter the public IP address of either worker node followed by the NodePort. For example:
http://<Public_IPv4_of_Node>:30080.
%% %%
Issue: curl ClusterIP
Failure
ClusterIP's IPTo curl
Solution Security Group in EC2 was set to
All TCP0-65535from0.0.0.0. Changed it toAll traffic
%%
I create an Ingress rule by crafting an ingress.yaml file with the following content:
Followed Kubernetes Doc
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: minimal-ingress
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
spec:
ingressClassName: nginx
rules:
- http:
paths:
- path: /nginx
pathType: Prefix
backend:
service:
name: my-nginx-deployment
port:
number: 80After creating the ingress.yaml file, I apply it to my cluster:
kubectl apply -f ingress.yaml%%
Question Issue: ingress path NOT working
<IP>/nginxIssue was found looking at logs of the ingress-controller-pod Finding pod:
kubectl get pods --all-namespacesOnce identified:kubectl logs ingress-nginx-controller-6f6c84b8-qftv2 -n ingress-nginx, where-nis for namespaceFailure ingress class
The log returned error related it to
7 store.go:431] "Ignoring ingress because of error while validating ingress class" ingress="default/minimal-ingress" error="no object matching key \"nginx-example\" in local store"The
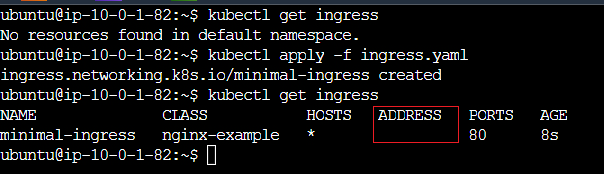
ingressClassName:portion of the .yaml Before I had a random name from sample file that did not exist later I removed it thinking it will default to something that work (it did not)Solution
kubectl get ingressclassto get list ofingressclass, i had only 1nginx. Updated the ingress.yamlUsed
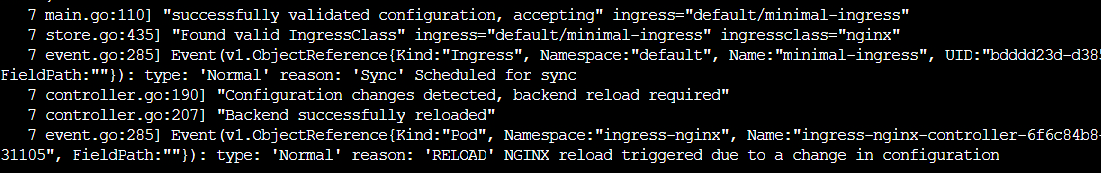
ingressClassName: nginxLog when working
When the ingress wasn’t working ADDRESS was empty
 %%
%%
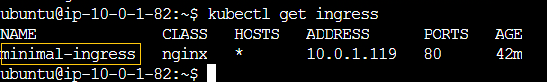
I verify the ingress was created:
Success
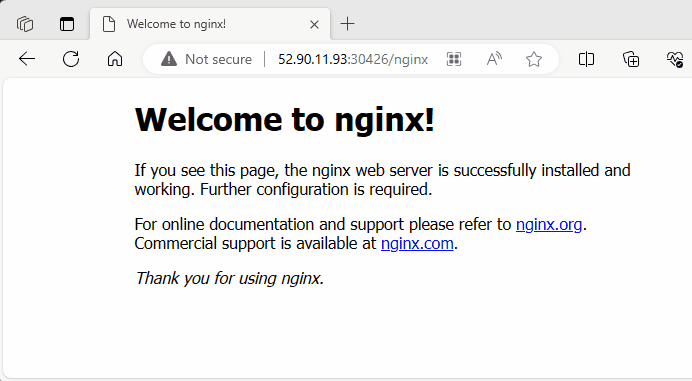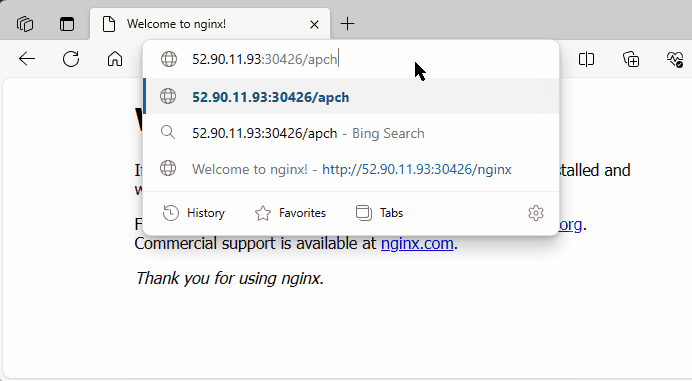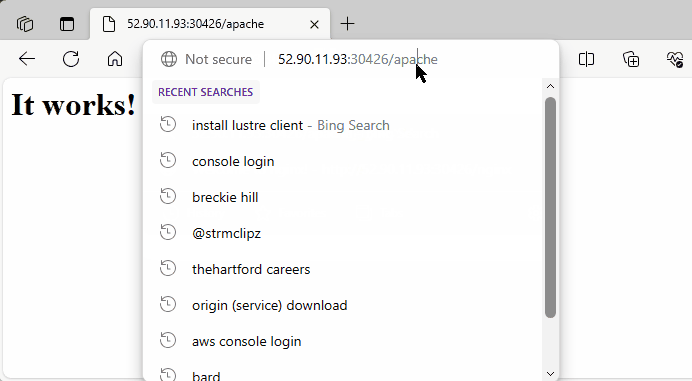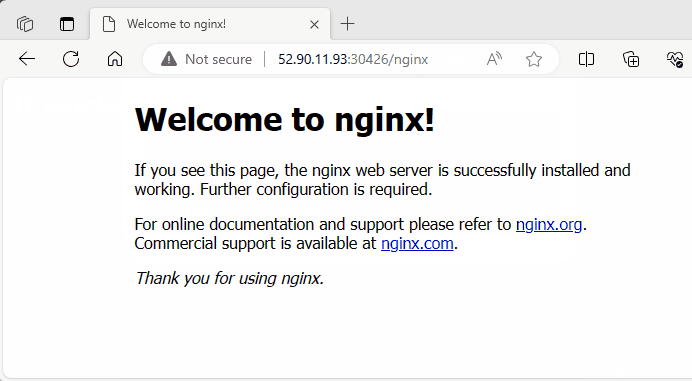
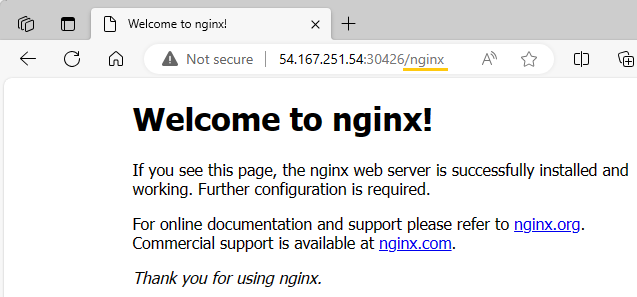
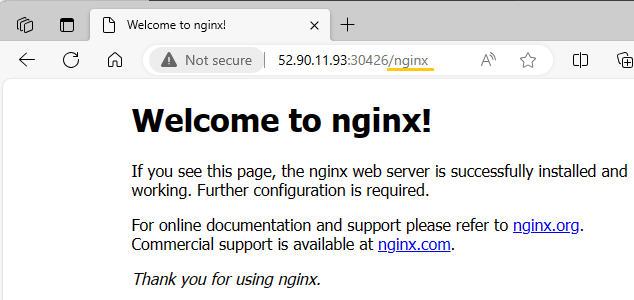
I test the ingress path /nginx using both the public IP addresses of worker nodes 1 and 2, along with the NodePort 30426.
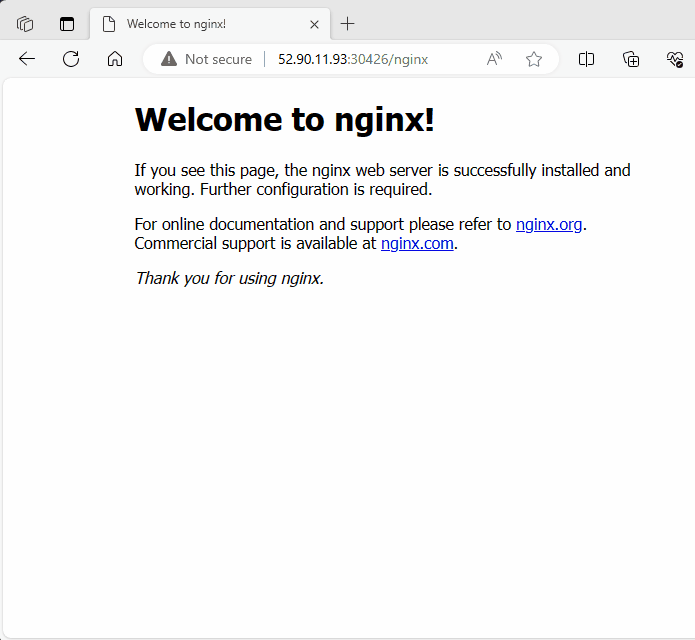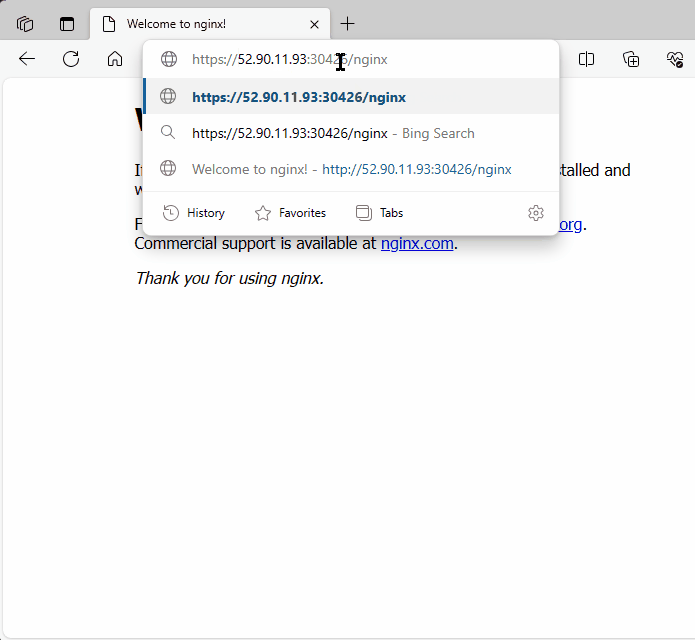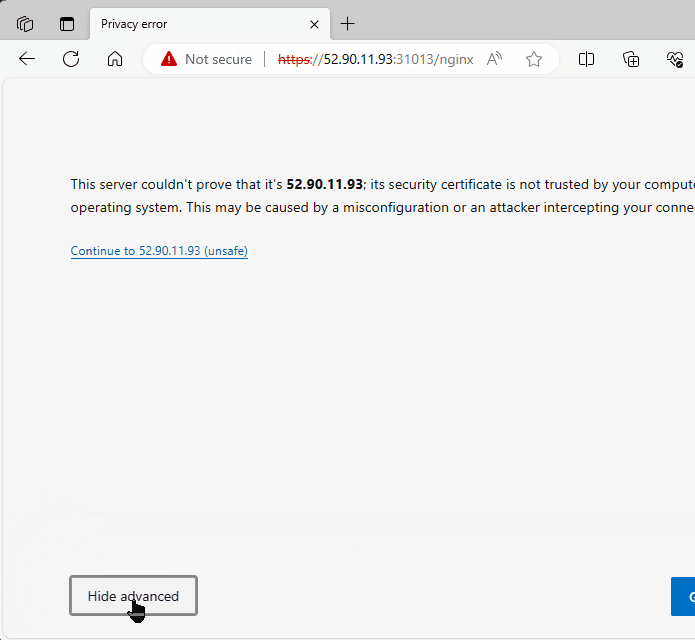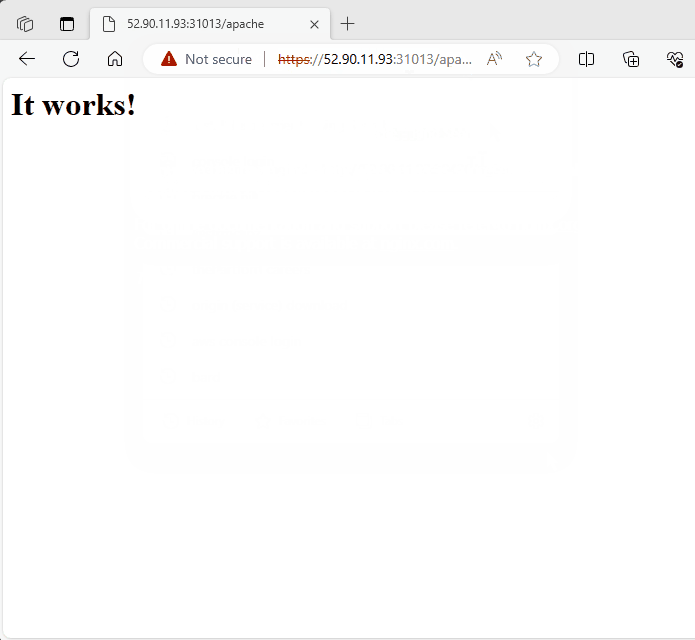
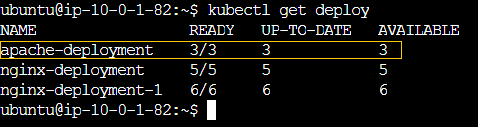
I will now create an Apache deployment along with a corresponding ClusterIP service to further test our Ingress.
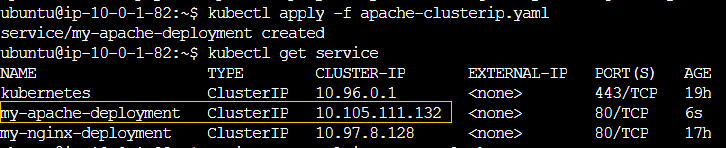
I have updated ingress.yaml to include an additional path /apache with the following configuration.
- path: /apache
pathType: Prefix
backend:
service:
name: my-apache-deployment
port:
number: 80I will now apply it again:
kubectl apply -f ingress.yaml
We can also try with the NodePort for https as per 80:30426 443:31013
Now, I will test both paths with both NodePorts mapped to port 80 for HTTP and port 443 for HTTPS.
Success
Using 80(HTTP) : NodePort
30426
Success
Using 443(HTTPS) : NodePort
31013
Warning
The ingress rule is configured with
pathType: Prefix. This means that, for example, both/nginxand/nginx123will match the rule, but/123nginxwill not be a match.
%%
Notes: Incase needed
ubuntu@ip-10-0-1-82:~$ cat apache-clusterip.yaml apiVersion: v1 kind: Service metadata: name: my-apache-deployment spec: type: ClusterIP ports: - targetPort: 80 port: 80 selector: app: apache ubuntu@ip-10-0-1-82:~$
ubuntu@ip-10-0-1-82:~$ cat apache-deployment.yaml apiVersion: apps/v1 kind: Deployment metadata: name: apache-deployment labels: app: apache spec: replicas: 3 selector: matchLabels: app: apache template: metadata: labels: app: apache spec: containers: - name: apache image: httpd ports: - containerPort: 80 ubuntu@ip-10-0-1-82:~$
ubuntu@ip-10-0-1-82:~$ cat ingress.yaml apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: minimal-ingress annotations: nginx.ingress.kubernetes.io/rewrite-target: / spec: ingressClassName: nginx rules: - http: paths: - path: /nginx pathType: Prefix backend: service: name: my-nginx-deployment port: number: 80 - path: /apache pathType: Prefix backend: service: name: my-apache-deployment port: number: 80 ubuntu@ip-10-0-1-82:~$
%%